Author: Ankit Baid, Research Analyst at Affluence Advisory
- CURRENT PROTOCOLS FOR NBFCs:
Under the current system, there were dozens of directives and alerts regulating the realm of space, which were considered outdated given the evolving environment. The deficiency of the current structure is highlighted by the fact that Indian banks documented 200+ data breaches in 2022—an astounding 20 percent of the global sum. This prompted the RBI to reassess the IT governance and cybersecurity framework for the financial industry. Source – The Hindu
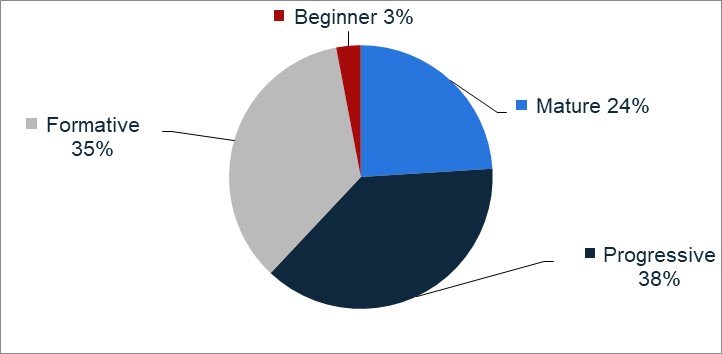
*As of 2022, only 24 percent of businesses and organizations in India were fully equipped to handle their own cybersecurity concerns, according to the CISCO Cybersecurity Readiness Index. Meanwhile, over 30 percent were still in the formative phase of readiness
- Challenges in the Financial Sector: The recent regulatory actions by the Reserve Bank of India against various banks and Non-Banking Financial Companies (NBFCs) have highlighted the critical importance of robust IT systems. Instances of IT system gaps have led to regulatory scrutiny and actions, impacting customer on-boarding and service offerings.
- Regulatory Scrutiny: The RBI’s actions against Kotak Mahindra Bank and other financial entities underscore the need for stringent IT governance and controls to ensure the security and resilience of IT systems within the financial sector.
- Industry Incidents: This wasn’t a one off case, but the industry has seen it across various banks and NBFC coming under the RBI’s scrutiny.
- HDFC BANK – Dec 2020 (Multiple glitches linked to digital banking, cards and payments)
- American Express – April 2021 (Non-compliant on storage of payment system data)
- Master Card – July 2021 (Non-compliance with data storage regulation)
- M&M Finance – Sept 2022 ( Material supervisory concern)
- Bajaj Finance – Nov 2023 ( Non- adherence with central banks digital lending guidelines)
- Paytm Payment ban – Jan 2024 ( Significant KYC irregularities)
- JM Financials – March 2024 (Serious deficiencies observed in its loan sanctioning process)
- IIFL Finance – March 2024 ( Material supervisory concerns)
- Kotak Bank – April 2024 – ( Data Security concern and deficient IT infrastructure)

*India witnesses 18% surge in weekly cyber-attacks in Q1 2023
More than 1.3 million cyber-attacks were reported across India in 2022. This was a significant increase compared to 2019. The country was amongst the top five with the most number of cyber security incidents that year. Furthermore, India’s ranked third in terms of internet user numbers and there by RBI had issues Master Direction on Information Technology Governance to bolster the risk management capabilities of financial institution in India.
Also Read: Scale-Based Regulation (SBR) 2023 for All Non-Banking Financial Companies (NBFC)
- THE RBI’S MASTER DIRECTION ON INFORMATION TECHNOLOGY GOVERNANCE, RISK, CONTROLS, AND ASSURANCE PRACTICES, 2023
Overview: The banker’s bank has issued the Master Direction on Information Technology Governance, Risk, Controls, and Assurance Practices, 2023, which outlines the guidelines for Information Technology (IT) Governance and Controls, Business Continuity Management, and Information Systems Audit for various financial institutions, including Non-Banking Financial Companies (NBFCs). This Master Direction aims to update and consolidate the existing instructions related to IT Governance and Controls, thereby ensuring a robust framework for managing IT-related risks and ensuring the security and resilience of IT systems within the financial sector.
As per the Central banks notice, NBFCs are required to establish a comprehensive IT Governance Framework that aligns with the strategic objectives of the organization and effectively manages IT-related risks. The key focus areas of the IT Governance Framework include strategic alignment, risk management, resource management, performance management, and Business Continuity/Disaster Recovery Management. This framework is designed to specify the governance structure and processes necessary to meet the business/strategic objectives of the NBFCs, as well as to define the roles and responsibilities of the Board of Directors, Senior Management, and IT Steering Committee.
Furthermore, the Master Direction emphasizes the importance of establishing an Enterprise-wide risk management policy or operational risk management policy that incorporates periodic assessment of IT-related risks, both inherent and potential risks. This policy is essential for ensuring accountability and mitigation of IT and cyber/information security risks within NBFCs.
In addition to the IT Governance Framework, the Master Direction also outlines the requirements for IT Infrastructure & Services Management, IT and Information Security Risk Management, and Business Continuity and Disaster Recovery Management. These requirements include guidelines for IT Services Management, Third-Party Arrangements, Capacity Management, Project Management, Change and Patch Management, Data Migration Controls, Audit Trails, Cryptographic controls, Physical and Environmental Controls, Access Controls, Controls on Teleworking, and Metrics.
- Elevated Responsibility and Supervision by Board and Senior Leadership
One of the primary consequences is the heightened responsibility and oversight demanded from the Board of Directors and top management concerning technology strategy and cybersecurity. According to the central banks directives, the Board will be tasked with endorsing IT strategy, security protocols, cyber crisis management blueprints, and continuity strategies. This reflects a clear acknowledgment of the importance of IT systems for delivering customer service through various platforms and the increasing influence of cyber threats on business resilience.
Previously, boards of financial institutions primarily concentrated on business, financial, and credit hazards. However, the extensive integration of technology in the industry signifies that boards can no longer afford to take a hands-off stance towards IT governance and security. Directors will now need to acquire expertise on technology blueprints, cyber threats, resilience investments, and routinely scrutinize reports from the IT strategy committee and the Chief Information Security Officer.
Financial institutions must also form a specialized IT strategy committee consisting of a minimum of three directors. It is required that the head of this committee be an independent director with substantial expertise in managing technology projects. This guarantees that IT investments and strategies are overseen with competency as a priority.
At the senior management tier, the guidelines amplify responsibility to ensure the execution of the IT strategy approved by the board and the effective reinforcement of cybersecurity protocols and measures. Additionally, the risk management function is required to closely collaborate with IT and information security teams while providing regular updates to the board.
- Requirement for Strong IT Governance Structures
A fundamental aspect of the master direction is the requirement for regulated entities to institute robust IT governance frameworks encompassing vision, strategy, risk management, resource utilization, performance evaluation, and business continuity.
Distinct ownership of IT strategy and cybersecurity must be delineated across board committees, senior management, and IT leadership. The directives also dictate the establishment of an IT steering committee comprising both business and technology divisions to supervise IT risk management, project execution, architectural standards, etc., under the oversight of senior management.
Presently, many financial entities in India possess makeshift IT governance structures with ambiguous responsibilities. Additionally, technology investments often fail to align with long-term business objectives. The Central banks new master direction will necessitate a significant overhaul of IT governance with a comprehensive framework. Matters such as IT-business synchronization, resource allocation, and competency enhancement will demand strategic deliberations between Chief Information Officers and business executives.
- Amplified Emphasis on Risk Evaluations and Management
The Central Banks notice signifies necessitates the IT risks to be formally identified, evaluated, and assimilated into the enterprise-wide risk management policy and framework. Cyber threats are no longer isolated but integrated into the overarching risk spectrum.
Financial entities must clearly outline the IT and cyber risk landscape based on their business operations, technology adoptions, digital platforms provided to clients, and threat scenarios. Furthermore, roles and responsibilities for IT risk management at operational levels necessitate elaboration.
Significantly, these risks must be monitored and regularly reported to the IT strategy committee and the board. Risk appetite declarations must also quantify tolerance for IT risks, with resource allocations made accordingly. This entails close collaboration between the IT and risk teams, spanning from risk identification to quarterly reporting.
- Strengthening Cybersecurity Measures
In the updated Central Banks guidelines, there’s a heightened emphasis on enhancing cybersecurity capabilities. Regulated entities are now required to fortify their cybersecurity defenses across various fronts, as detailed below:
- Recruiting or training skilled professionals for continuous security monitoring, threat detection, incident response, and digital forensics.
- Establishing robust Security Operations Centers (SOCs) to manage security operations effectively.
- Deploying 24/7 monitoring for network and endpoint threats, intrusion prevention, vulnerability management, and privileged access control.
- Conducting regular assessments of cyber risks and controls, including vulnerability scans and penetration tests.
- Implementing multi-factor authentication for critical systems, remote access, and privileged users.
- Developing protocols for cyber crisis management and incident response, with clearly defined procedures.
- Vigilantly tracking security events and incidents for root cause analysis and remediation.
- Promptly reporting significant incidents to CERT-In and RBI in accordance with guidelines.
- Enhancing business Resilience and Disaster Recovery Readiness
The Central banker has outlined directives for financial institutions to evaluate the business impact and establish suitable recovery time and recovery point objectives for critical IT systems and applications. This directive stems from the necessity to maintain uninterrupted banking services for customers even during disruptions.
For essential applications such as core banking systems, the guidelines advocate that there should be no data loss i.e. Recovery Point Objectives (RPO) and very minimal downtime Recovery Time Objectives (RTO) during disaster/disruption. Achieving this entails data mirroring across Data Centers (DC) and Data Recovery (DR) sites, along with system that can clearly switch over in case of problem. Banks are required to evaluate their current Business Continuity (BC) and Disaster Recovery (DR) arrangements against RBI guidance. Any deficiencies, such as lack of data replicas or untested failover plans, will necessitate significant investments.
Moreover, the guidelines mandate biannual disaster recovery drills and testing of BC plans under various scenarios. Any issues identified during DR tests must be promptly addressed.
- Strengthening Oversight of Third-Party Technology Risks
Financial institutions increasingly rely on technology vendors, leveraging fintech, cloud service providers, and managed security service providers for rapid innovation and cost efficiencies. However, this reliance on third-party entities might introduces associated risks, as highlighted by the RBI.
Regulated entities must conduct more frequent assessments of supplier risks and develop capabilities for effective vendor management. Contracts with third parties should enforce compliance with RBI guidelines on security, availability, and confidentiality. Collaborative testing to validate service levels and resilience capabilities must also be established.
For critical IT services outsourced, the RBI mandates the maintenance of source code escrows to mitigate vendor lock-in risks. Additionally, change management controls and vulnerability assessments apply to third-party managed systems.
- Ramping Up IT Audit Frequency and Coverage
Due to the considerable monetary investments made in technology and the risks involved, the central banks places a much stronger emphasis on frequency and scope of IT audits. Regulated entities are advised to adopt a risk-based approach to information systems audits, covering aspects of IT governance, controls, and security. Continuous IT audits leveraging automation are recommended, particularly for core banking and critical systems.
The audit committee of the board is entrusted with overseeing IT audit findings, tracking issues, and recommending corrective measures. Key focus areas should include cybersecurity, access controls, DR readiness, and vendor risks. Utilizing external audit resources is permissible in cases where in-house expertise is lacking.
There by with this initiative a comprehensive assurance to the board regarding the effectiveness of technology controls and cyber resilience initiatives.
Challenges:
- Technology Investment
- Limited talent pool network
- Technology evolution outpaces implementation
- Internal Team preparedness
Benefits:
- Data Protection and Privacy
- Cyber-security no more operating as a silo, there by better integration in the system and awareness amongst the stakeholder
- Digital Transaction scalability
- Financial Eco-system will be strengthen leveraging tech and data
Future IT implementation:
- Block chain
- Neo- Banking
- Open- Banking
- KEY HIGHLIGHTS – RBI’S MASTER DIRECTION 2023
IT Governance Framework
- Risk Management
- Resource Management
- Business continuity / Disaster recovery management
Board Level IT strategy committee
- Establish Board level IT Strategy Committee (ITSC)
Role of Board of Directors
- The strategies and policies related to IT, Information Assets, Business Continuity, Information Security, and Cyber Security (including Incident Response and Recovery Management / Cyber Crisis Management) shall be approved by the Board of Directors.
Third-party Arrangement
- REs shall, put in place appropriate vendor risk assessment process and controls proportionate to the assessed risk and materiality
Data migration and control
- REs shall have a documented data migration policy specifying a systematic process for data migration, ensuring data integrity, completeness and consistency.
IT and Information security Risk Management
- Periodic review of IT related risks
- Conduct of Vulnerability Assessment (VA) / Penetration Testing (PT)
Business Continuity and Disaster Recovery Management
- The BCP and DR policy shall adopt best practices18 to guide its actions in reducing the likelihood or impact of the disruptive incidents and maintaining business continuity.
Disclaimer: This article provides general information existing at the time of preparation and we take no responsibility to update it with the subsequent changes in the law. The article is intended as a news update and Affluence Advisory neither assumes nor accepts any responsibility for any loss arising to any person acting or refraining from acting as a result of any material contained in this article. It is recommended that professional advice be taken based on specific facts and circumstances. This article does not substitute the need to refer to the original pronouncement
CLICK HERE DOWNLOAD PDF